In the labyrinthine landscape of cybersecurity, insider threats loom as a formidable challenge, demanding proactive measures to safeguard sensitive data and critical infrastructure. Insider Threat Awareness Answers 2023 emerges as an indispensable guide, providing a comprehensive exploration of this pressing issue.
This comprehensive resource unravels the intricate web of insider threats, empowering organizations with actionable insights to effectively detect, prevent, and mitigate these malicious actors from within.
Insider Threat Awareness Landscape 2023: Insider Threat Awareness Answers 2023
The insider threat landscape is constantly evolving, with new trends and patterns emerging all the time. In 2023, we can expect to see a continued increase in the number of insider threats, as well as a shift towards more sophisticated and targeted attacks.
The insider threat landscape is becoming increasingly complex, with a growing number of factors contributing to the risk of insider threats. These factors include the increasing use of technology, the globalization of the workforce, and the rise of social media.
According to a recent study by the Ponemon Institute, the average cost of an insider threat incident is $11.45 million. Insider threats can also have a significant impact on an organization’s reputation, customer trust, and employee morale.
Emerging Trends and Patterns in Insider Threats, Insider threat awareness answers 2023
- Insider threats are becoming more sophisticated and targeted.
- Insider threats are increasingly being used for financial gain.
- Insider threats are becoming more difficult to detect and prevent.
- Insider threats are a growing concern for organizations of all sizes.
Types of Insider Threats

There are many different types of insider threats, but they can be broadly classified into two categories: malicious and non-malicious.
Malicious Insider Threats
- Sabotage:This is the most serious type of insider threat, and it involves an insider intentionally damaging or destroying an organization’s assets.
- Theft:This involves an insider stealing an organization’s assets, such as data, money, or equipment.
- Espionage:This involves an insider spying on an organization and gathering sensitive information.
- Fraud:This involves an insider using their position to commit fraud, such as embezzlement or identity theft.
Non-Malicious Insider Threats
- Negligence:This is the most common type of insider threat, and it involves an insider unintentionally causing harm to an organization. For example, an employee may accidentally delete important files or click on a malicious link in an email.
- Mistakes:These are similar to negligence, but they are typically more serious and can have a greater impact on an organization.
- Disgruntled employees:These are employees who are unhappy with their jobs and may be more likely to engage in insider threats.
Insider Threat Detection and Prevention

There are a number of things that organizations can do to detect and prevent insider threats. These include:
Technology
- User activity monitoring (UAM):This technology can be used to track the activities of users on an organization’s network. This can help to identify suspicious activity that may indicate an insider threat.
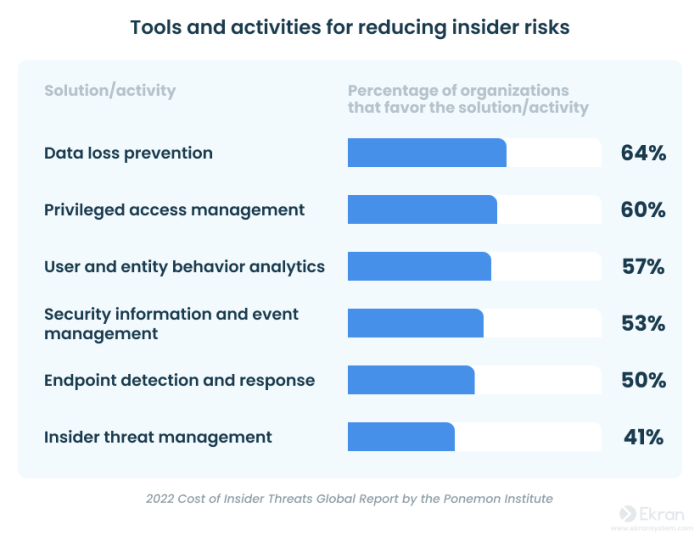
- Data loss prevention (DLP):This technology can be used to prevent users from exfiltrating sensitive data from an organization’s network.
- Endpoint security:This technology can be used to protect endpoints, such as laptops and desktops, from malware and other threats.
Human Intelligence
- Insider threat awareness training:This training can help employees to understand the insider threat and how to protect themselves from it.
- Employee screening:This can help to identify potential insider threats before they are hired.
- Background checks:These can help to identify potential insider threats who have a history of criminal activity.
Risk Management
- Insider threat risk assessment:This can help to identify the insider threats that an organization is most vulnerable to.
- Insider threat response plan:This plan should Artikel the steps that an organization will take in the event of an insider threat incident.
- Insider threat program:This program should be designed to manage the insider threat risk on an ongoing basis.
Insider Threat Response and Mitigation
In the event of an insider threat incident, it is important to take the following steps:
Containment
- Identify and isolate the insider threat actor.
- Secure the affected systems and data.
- Preserve evidence for investigation.
Investigation
- Determine the scope and impact of the insider threat incident.
- Identify the root cause of the insider threat incident.
- Recommend steps to prevent similar incidents from occurring in the future.
Remediation
- Take disciplinary action against the insider threat actor.
- Implement new security measures to prevent similar incidents from occurring.
- Provide support to victims of the insider threat incident.
Insider Threat Awareness Training
Insider threat awareness training is an important part of any insider threat prevention program. This training can help employees to understand the insider threat and how to protect themselves from it. Insider threat awareness training should be tailored to the specific needs of an organization and its employees.
Target Audience for Insider Threat Awareness Training
- All employees
- Contractors
- Vendors
- Business partners
Tips and Best Practices for Effective Insider Threat Awareness Training Programs
- Make the training interactive and engaging.
- Use real-world examples to illustrate the insider threat.
- Provide employees with the tools and resources they need to protect themselves from the insider threat.
- Test employees’ knowledge of the insider threat on a regular basis.
Insider Threat Awareness Resources
| Resource | Description | Link |
|---|---|---|
| Insider Threat Center | The Insider Threat Center is a resource for information on insider threats. The center provides information on the latest insider threat trends, best practices for insider threat prevention, and case studies of insider threat incidents. | https://www.dhs.gov/topic/insider-threat |
| Insider Threat Hub | The Insider Threat Hub is a resource for information on insider threats. The hub provides information on the latest insider threat trends, best practices for insider threat prevention, and case studies of insider threat incidents. | https://www.cisa.gov/topics/insider-threat |
| Insider Threat Playbook | The Insider Threat Playbook is a resource for organizations on how to develop and implement an insider threat prevention program. The playbook provides guidance on how to identify insider threats, assess the insider threat risk, and implement security measures to prevent insider threat incidents. | https://www.mitre.org/publications/technical-papers/insider-threat-playbook |
FAQ Summary
What are the most common types of insider threats?
Insider threats can manifest in various forms, including disgruntled employees, malicious actors seeking financial gain, or individuals with compromised credentials.
How can organizations detect and prevent insider threats?
Effective insider threat detection and prevention strategies involve a combination of technological solutions, human intelligence, and robust risk management practices.
What are the key elements of an insider threat response plan?
A comprehensive insider threat response plan should encompass containment, investigation, remediation, and communication protocols to effectively manage and mitigate potential incidents.
Why is insider threat awareness training crucial?
Insider threat awareness training empowers employees to recognize and report suspicious activities, fostering a culture of vigilance and collective responsibility for cybersecurity.